Here are my welcoming remarks to the Data Privacy and Integrity Advisory Committee of the Department of Homeland Security, which is holding a public hearing at Harvard Law School today.
Ladies and Gentleman:
Welcome to Harvard Law School A law professor’s job is often to frame and state a question.
Our world is changing. No surprise in this. Yet the pace of change comes to many as surprise. Technology is changing the world faster than it ever changed before. A speaker at the Berkman Center yesterday, JD Lasica, said “We’re living in extraordinary times — media will change more in the next five years than it has in the past 50.” He spoke about ourmedia, an entity formed nonprofit just a few weeks ago, with now twenty two thousand members contributing their work and energy to the creation of a shared media space, grassroots expression of cooperative spirit, growth like lightning.
Success in our cyber future will come to those with the most astute conceptual technological strategy. I beleive this is true for individuals, for businesses, for universities, for nations. This is a challenge for anyone in a leadership position, clearly the challenge for you as you face the task of recommending measures for the security of our homeland. Think cyber strategy for homeland security.
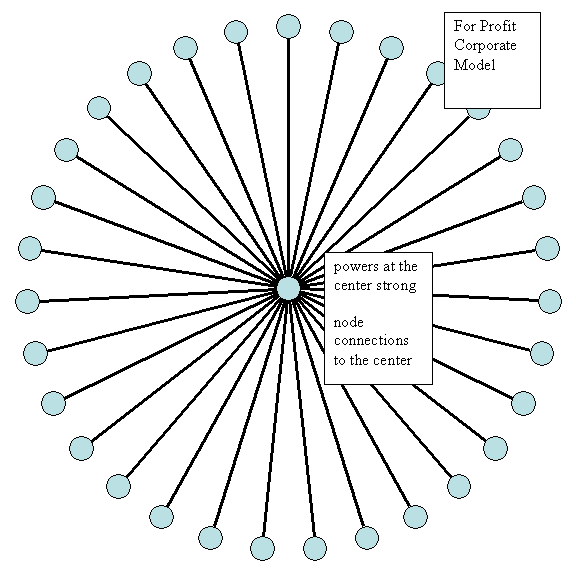
Cyberspace, our future environment, is a networked space of nodes, each able to connect with any other, to send message, to receive. From the viewpoint of the user sitting at the screen pointing and clicking through the space there is no geographic boundary. Boundaries are instead passwords, boxes you have to fill or click, boundaries of language.
In cyberspace, brand is everything,for business as well as nation,. Identity is capital.The cyber power to connect with you and listen to your message is in the users hands. Who are users? All of us, not just republicans or democrats, or Americans. All the world’s a stage on which identity plays.
Consider privacy from the viewpoint of the user. Are you huddled in a room behind locked doors moving on the screen only to places that are predetermined to be safe? Do you exist in a closed world? This is one view of privacy. Privacy as prison. Prison as security.
Another is, you live in culture of trust, a neighborhood where your doors are open, your children free to run. You sit at your screen and go where ever you want to go.
Consider the necker cube. Take it as a methphor for the deepest dispute your client faces. Your client sees himself and his dispute one way. Your client’s enemy sees herself and her dispute another. Can it be seen both ways at the same time?
The logic of the equation so painfully taught to us by Osama Bin Laden dictates that our security is not merely a function of the defenses we put up. Our security is equally if not more a function of the hostility to us beyond our borders. If hostility continues to rise, our quest for security will be defeated. Privacy will become a form of that room with the locked door, security recast as privacy, and privacy a prison.
If that hostility is diminishes, then our security and our privacy will grow.
What would be a *cyber* strategy to diminish the hostility to the United States of America in the world beyond.



 This morning when I went to show Roberto the entry on my blog with our audio interview, to my complete bafflement the blog entry for Mangabeira is gone! Some genie in the bottle, computer gods once again at work. In any event here again,
This morning when I went to show Roberto the entry on my blog with our audio interview, to my complete bafflement the blog entry for Mangabeira is gone! Some genie in the bottle, computer gods once again at work. In any event here again,